Web application firewalls (WAFs) and standard firewalls play a critical role in network security. No matter the size of a network, these measures of security must be in place to ensure the utmost safety of not only the individual user but of sensitive data and entire networks and infrastructures.
What is the difference between a web application firewall and a firewall? A web application firewall (WAF) provides protection against publicly exposed services, like web applications, APIs to Web Hooks. Attacks can include SQL injection, cross site scripting to broken authentication and access control attacks. Whilst a firewall protects against attacks from network by controlling, prohibiting or inspecting network traffic for malicious attacks.
Web application firewalls and standard firewalls not only differ in the type of protection they offer but also in overall function. The remainder of this article will discuss other key differences between a WAF and a regular firewall.
10 Key Differences Between WAFs and Firewalls
1. While both are firewalls, they’re functionality is different.
To understand what makes WAF and a Firewall different, it is best to first understand what a WAF and a Firewall is.
A WAF is a firewall primarily used for protecting applications, APIs to Webhooks, providing protection by assessing what the traffic is trying to do and blocking it if necessary, especially if the actions in the traffic are deemed malicious.
used to sift through data, monitoring, and (sometimes) blocking traffic coming from or going to the application. A firewall, on the other hand, is used to serve as a border of security between a trusted network and an untrusted network.
For the most part, WAF is primarily focused on the security of an application, whereas the traditional firewall is focused on the security of a network.
2. WAFs and firewalls are used in different locations on the network.
Generally, a standard firewall is placed on the edge of the network, acting as a barrier inbetween trusted networks and those networks that are considered unknown and therefore untrusted.
WAFs are placed before applications offering protection from threats that can attack applications. This is the primary difference in the way they are used and dictates the primary roles of each.
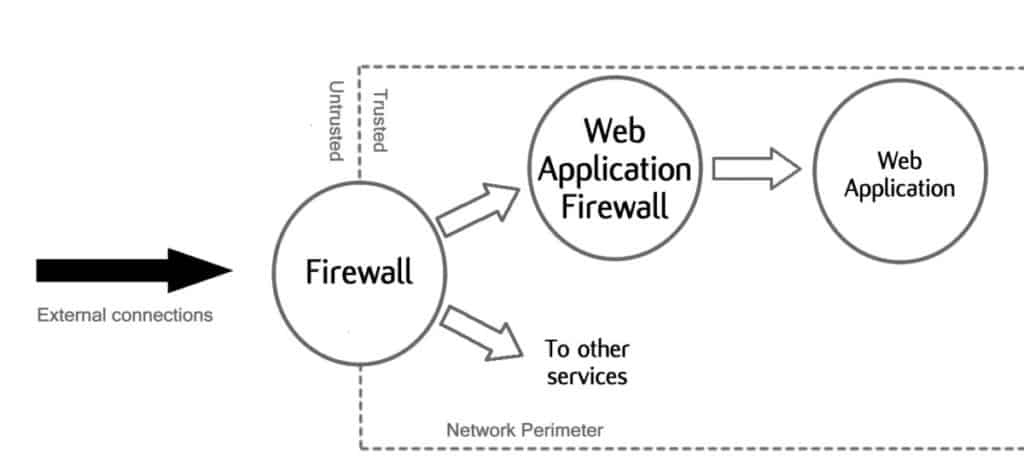
Firewalls act much in the same way that a country’s border acts: scanning for things that are not allowed to come in or out. WAF acts in a similar manner but more oriented to the application-side of the network.
3. WAFs and firewalls protect against different threats.
Firewalls are generally designed to permit or deny access to a network, thus preventing attacks from unauthorized permission. Examples of a firewall doing this include blocking pornography, unsuitable content, whilst permitting access can include logging into the local private corporate network.
WAFs main focus is on threats aimed at applications by providing a layer of defence against threats including:
- SQL injection attacks
- Cross site (XSS) scripting attacks
- Authentication attacks like broken access

4. Both WAFs and firewalls represent different OSI model layers
The OSI model is a graphic representation of the inner-workings and function of a network. It could be considered the encyclopedic map of the network.
Firewalls typically focus on the network and transport layer, OSI layer 3 and layer 4 respectively. Layer 3 concentrates on network packets and their transfer across the network nodes. Layer 4 concerns the transfer of data from the source to the destination.
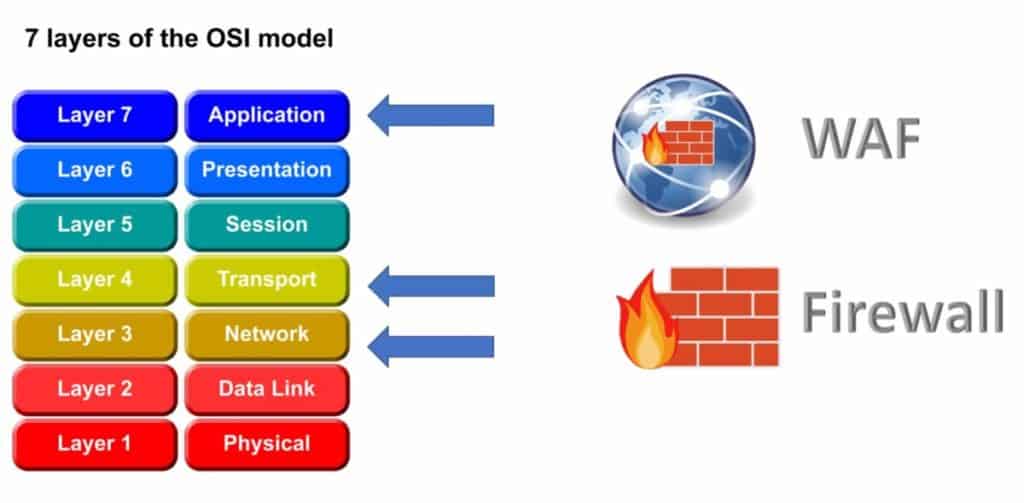
WAF’s focus is primarily on application layer, layer 7. Layer 7 focuses on the interaction from the user, using the application and it’s interface to communicate across the network.
5. Each differs in the level of access control on offer
Because a WAF’s primary function does not include limiting or restricting access or permissions to a network, it does not offer access control. This, however, is one of the standard firewall’s primary functions.
The access control settings are often customizable to suit the user’s needs. Often, a firewall will deny access by default, so only those who are authorized can access the relevant websites, files, folders and network services.
6. WAFs and firewalls use different algorithmic approaches
WAFs and Firewalls are designed primarily to do different jobs even though there is some overlap and to these job effectively, the way each one of these works including the algorithms they use can differ.
This holds true, as WAFs run different algorithms to detect anomalies, check heuristics and match signature based patterns. General firewalls, on the other hand, run algorithms to work as proxies, inspect network packets using stateless and stateful techniques to using packet filtering techniques.
These algorithms essentially define the key roles that each the WAF and Firewall play in the network.
7. WAFs and Firewalls offer different types of DDOS protection.
Distributed Denial of Service (DDoS) attacks, are the type of attacks that can leave a network crippled and in critical condition. The DDoS attack overloads networks and services stopping legitimate access uisng techniques to flood services with garbage packets and information.
Both of these different types of firewalls can help in protecting against DDOS attacks; however, the location or focus of the protection is markedly different between each one. As WAFs deal primarily with applications, the level of DDOS protection provided focuses on the application layer (OSI layer 7).
Similarly, since the standard firewall’s focus is on the base levels of the network (OSI layer 3 and layer 4), DDOS protection is focused at network layer.
8. WAFs and firewalls have different operational modes
A WAF is able to operate in two distinct modes: Passive Mode and Active Inspection.
- Passive Mode essentially means that the WAF operates without taking action and observes only. This mode is fine for testing but should not be used in real working production state environments.
- Active Inspection Mode essentially means the WAF will act upon threats by scanning continously the application traffic, checking for threats and malicious actions.
A standard Firewall uses Routed Mode and Transparent Mode.
- Routed Mode follows OSI layer 3 and is the main operational mode, that works at OSI layer 3 where it acts like a route processing routing protocols.
- Transparent Mode follows OSI layer 2 only whereby data is tranparently forwarded.
9. WAFs and firewalls have different application level protection.
Because they are different in the way they are designed, the functions they provide, and where they are located. WAFs and firewalls also differ in the amount of application level protection.
Firewalls are designed to operate at levels 3 and 4 of the OSI model, the focus of its protection is to be a gatekeeper for ingress and egress. This allows firewalls to focus on the data transfer between networks, validating addresses, and data packets.
A WAF’s works at the application layer (OSI level 7) of the network, thus providing security to the entire application layer of the network. The application layer includes web applications, APIs and Webhooks.
10. Each has a different use case.
The use cases for firewalls and WAFs is different as they offer different types of protection. WAFs are generally placed behind firewalls and protect web applications, APIs and Webhooks. They provide additional protection than a firewall would provide, protecting against specific application layer attacks.
Firewalls are designed to protect the outer perimeter and provide further protection between internal network layers to keep them segregated and protected. They are an access control mechanism, controlling what can come through, what can go out, with advanced firewalls also being able to inspect traffic and decide if it’s malicious or not using threat intelligence.
With multiple firewalls in place, a network becomes more secure, with strongholds against possible threats to numerous locations within it.
Cloud WAF
Many of the cloud providers have cloud enabled WAFs to protect web workloads on their cloud services. With customisable rules from OWASP Top 10 vulnerabilities to more detailed rules dealing with a range of threats.
- Amazon Web Services WAF
- Microsoft Azure Web Application Firewall
- Google Cloud Armor
- Cloudflare WAF
Content Distribution Networks also use WAFs to protect their customer’s web traffic with leaders in this field being Cloudflare and Akamai.
Conclusion
Web application firewalls and traditional firewalls, while similar in definition, are fundamentally different and designed with unique roles for a network.
Knowing the key differences between them is important to understand which solution is best for any scenario that may present itself when setting up a network—and be just the line of defense necessary to prevent a crippling cyber attack.
References:
https://serverfault.com/questions/432413/waf-vs-firewall
https://ipwithease.com/web-application-firewall-vs-network-firewall/
https://en.wikipedia.org/wiki/OSI_model
https://en.wikipedia.org/wiki/Network_layer
https://en.wikipedia.org/wiki/Application_layer

